Have you ever wondered how vulnerable your business is to cyberattacks? According to Verizon’s Data Breach Investigations Report, nearly 43% of cyberattacks target small businesses, often exploiting weak or outdated security measures.
One of the most effective ways to strengthen your cybersecurity posture is by implementing Multi-Factor Authentication (MFA). Even if a hacker gets your password, MFA adds a second—or third—layer of protection that can stop them in their tracks.
In this article, Graphene Technologies breaks down what MFA is, why it matters, and how to implement it for your small business. Let’s explore how you can take a crucial step toward securing your systems.
Why MFA Matters for Small Businesses
You might think hackers wouldn’t bother with a small company—but they do. In fact, small businesses are often easier targets because they lack advanced security systems. A single compromised password can open the door to financial loss, data theft, and reputational damage.
Fortunately, MFA helps by requiring users to provide two or more verification factors to access a system—making it significantly harder for cybercriminals to succeed. Moreover, it’s especially powerful against common threats like phishing, credential stuffing, and brute-force attacks.
For additional protection tips, check out our guide to Cybersecurity Services for Small Businesses.
What is Multi-Factor Authentication?
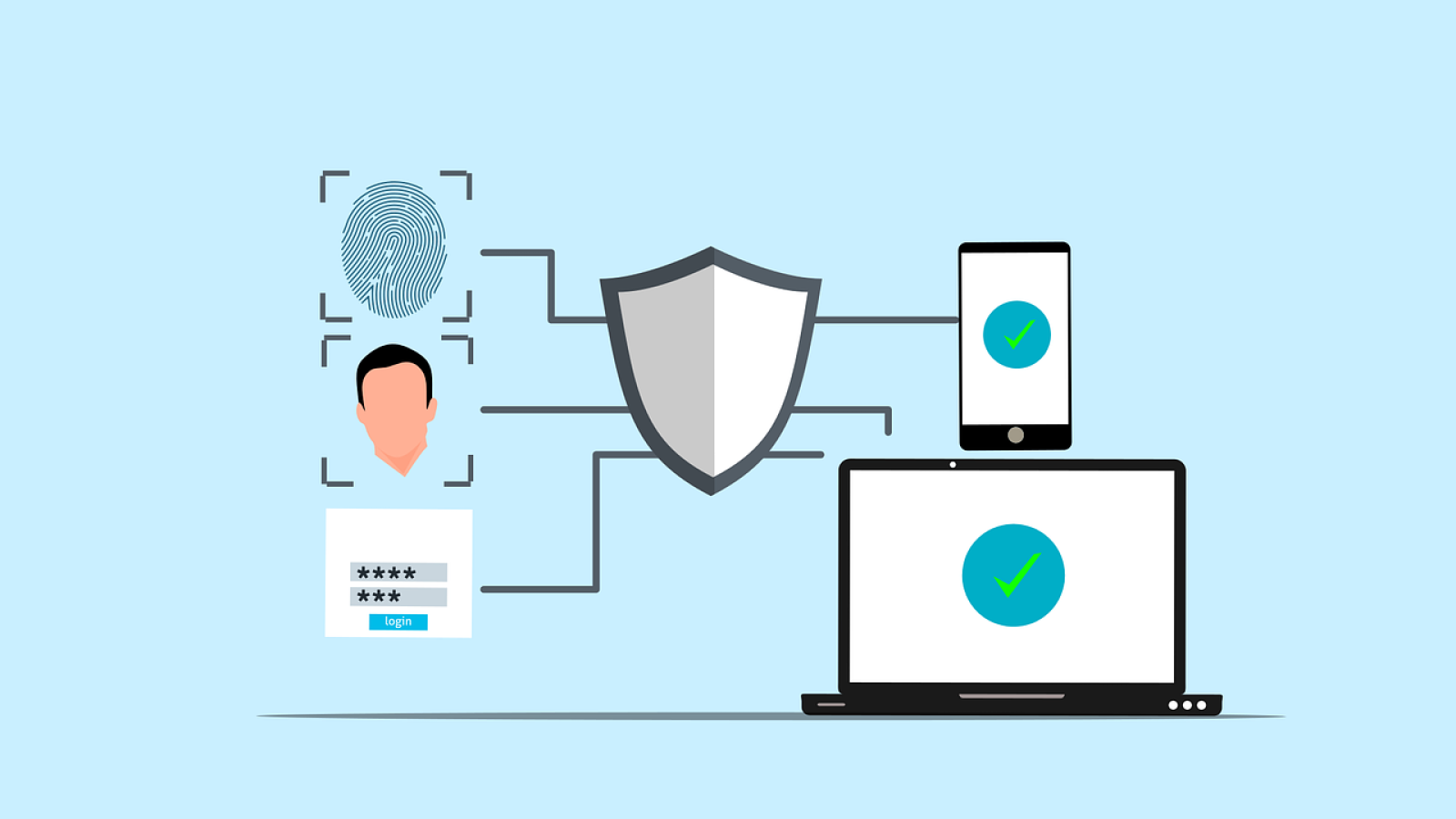
Multi-Factor Authentication is a security process that requires users to confirm their identity using multiple methods. Rather than relying on just a password, MFA adds layers of security.
1. Something You Know
This includes your password or PIN. It’s the most basic level, yet also the weakest if used alone.
2. Something You Have
This could be a phone, security token, or app generating time-based codes. For instance, tools like Google Authenticator provide rotating codes every 30 seconds.
3. Something You Are
This involves biometrics such as fingerprints or facial recognition. Because these factors are unique to each user, they’re very hard to fake.
When used together, these factors create a strong defense against unauthorized access. As a result, MFA becomes a highly effective way to enhance your business’s security posture.
How to Implement MFA in Your Small Business
Although it might sound complex, implementing MFA is manageable with the right approach. Here’s how to do it step by step:
Step 1: Assess Your Current Security Setup
Start by identifying your most sensitive systems:
-
Email accounts (e.g., Gmail, Outlook)
-
Cloud platforms (Microsoft 365, Google Workspace)
-
Financial tools (e.g., QuickBooks, online banking)
-
Customer databases and CRMs
If you’re unsure where to begin, our IT Consulting Services can help you audit and prioritize your security needs. Additionally, conducting a risk assessment ensures you cover your most vulnerable access points.
Step 2: Choose the Right MFA Solution
There are several user-friendly MFA tools available today. Consider these options:
-
Google Authenticator – Free and reliable.
-
Duo Security – Cloud-based and highly scalable.
-
Okta – Excellent for growing businesses.
-
Authy – Offers backup and cross-device syncing.
While each has its pros and cons, selecting the right solution comes down to business needs, size, and employee preferences. Furthermore, you should ensure your chosen tool is easy to deploy and compatible with your existing infrastructure.
Step 3: Roll Out MFA Across Critical Systems
Once you’ve selected a provider, it’s time to roll out MFA:
-
Start with critical platforms, such as email and CRM tools.
-
Require MFA for all employees, especially those with access to financial or customer data.
-
Implement MFA for remote access, using VPNs or secure gateways.
Moreover, plan your rollout in phases to minimize disruption and address any learning curves employees may experience.
Step 4: Train and Support Your Employees
Implementing MFA is only effective if your team knows how to use it. Therefore, training is essential:
-
Create step-by-step guides.
-
Host short demo sessions or webinars.
-
Offer helpdesk support for setup and troubleshooting.
In addition, emphasize the “why” behind MFA. When employees understand the risks and benefits, they’re more likely to adopt best practices.
You can also include MFA training as part of your Employee Cybersecurity Education Program.
Step 5: Monitor, Update, and Maintain
Cybersecurity is not static—it requires ongoing effort. That’s why continuous monitoring is key.
-
Update MFA methods regularly to adapt to new threats.
-
Revoke access immediately when employees leave.
-
Test recovery procedures for lost devices or access issues.
As a best practice, conduct quarterly security reviews to ensure MFA settings still align with your company’s growth and structure.
Common Challenges (and How to Solve Them)
While MFA is a strong solution, it’s not without hurdles. Thankfully, most can be resolved quickly.
1. Employee Resistance
Explain the benefits clearly. For instance, share real-world examples of breaches that MFA could have prevented. In addition, keep the process simple and convenient.
2. System Compatibility Issues
Some older apps may not support MFA. In these cases, consider using an identity provider like Okta or Duo to act as a bridge.
3. Cost Concerns
If budget is tight, start with free tools like Google Authenticator. Then, as your business scales, you can explore more robust paid options.
4. Lost or Stolen Devices
Always plan for device recovery. Many tools allow backup codes or secondary verification options. As a result, employees can regain access without compromising security.
Don’t Wait—Secure Your Business with MFA Today
In today’s digital world, it’s not enough to rely on passwords alone. Multi-Factor Authentication is a simple, cost-effective way to protect your company from breaches, data loss, and cybercrime.
To recap:
-
Start with an audit of your systems.
-
Choose an MFA tool that fits your team.
-
Roll it out systematically.
-
Provide support and training.
-
Monitor, review, and improve continuously.
If you’re ready to level up your business security, we’re here to help. Schedule a free consultation with Graphene Technologies in Houston, TX and let us help you build a safer, more resilient IT environment.
Add a Comment